Surveillance state spreads its wings
- By Zhao Jinglun
 0 Comment(s)
0 Comment(s) Print
Print E-mail China.org.cn, July 25, 2013
E-mail China.org.cn, July 25, 2013
![U.S. Army Gen. Keith Alexander, commander of the U.S. Cyber Command, director of National Security Agency (NSA), testifies before a Senate Appropriations Committee hearing in Washington D.C. on June 12, 2013. [Xinhua/Fang Zhe] U.S. Army Gen. Keith Alexander, commander of the U.S. Cyber Command, director of National Security Agency (NSA), testifies before a Senate Appropriations Committee hearing in Washington D.C. on June 12, 2013. [Xinhua/Fang Zhe]](http://images.china.cn/attachement/jpg/site1007/20130725/001ec949c22b135b06251b.jpg) |
|
U.S. Army Gen. Keith Alexander, commander of the U.S. Cyber Command, director of National Security Agency (NSA), testifies before a Senate Appropriations Committee hearing in Washington D.C. on June 12, 2013. [Xinhua/Fang Zhe] |
The U.S. National Security Agency's director, General Keith B. Alexander's thousands of spies want to "collect it all" – they want not just the needle, but the entire haystack, as one former U.S. intelligence official put it. A recent piece in the Washington Post about NSA director General Alexander hit the nail on the head. It said: "Alexander has pushed hard for everything he can get: Tools, resources and the legal authority to collect and store vast quantities of raw information on American and foreign communications."
No electronic communication can ever be free of U.S. collection and monitoring. Documents provided by Edward Snowden and published by the Guardian show that the NSA's goal is to collect, monitor and store every telephone and Internet communication. It already collects billions of calls and emails every single day. Mathematician William Binney has said that the NSA has "assembled in the order of twenty trillion transactions about U.S. citizens with other U.S. citizens." He added that "this estimate only involved phone calls and emails."
As Guardian columnist Glen Greenwald points out: "There is no legal authority for the NSA to do this."
Foreign Policy magazine recently carried an article by Matthew M. Aid which disclosed clandestine human intelligence missions, otherwise known as "black bag" operations, in which CIA clandestine operators surreptitiously gain access to the computer systems and email accounts of targets that are of high interest to American spies. The CIA's clandestine service conducts such black bag operations on behalf of the NSA. According to Aid, over the past decade clandestine operators have mounted more than 100 black bag jobs designed to penetrate foreign government and military communications and computer systems, especially those located in China.
But that is not all. According to bestselling author and journalist James Bamford, noted for his writings about U.S. intelligence agencies, General Alexander's 14,000 cyber warriors are ready to unleash hell to destabilize and exploit all nations. Using cyber-kinetic attacks, these warriors have the capability to physically destroy an adversary's equipment and infrastructure, and even to kill.
Following disclosures in the New York Times, it is now well known that the NSA, in partnership with the CIA and Israeli intelligence known as Unit 8200, developed the cyber weapon known as Stuxnet. The weapon was used to successfully attack and disable roughly 1,000 centrifuges at Iran's nuclear facility in Natanz.
According to Bamford, Stuxnet is only the beginning. The NSA has recruited thousands of computer experts, hackers and engineering PhDs to expand U.S. digital offensive capabilities. The Pentagon has requested $4.7 billion for cyberspace operations, in spite of sequestration. General Alexander is known as "Emperor Alexander," because whatever he wants, he gets.
Deputy Defense Secretary Ashton B. Carter disclosed on July 18 that the military was about to deploy roughly 4,000 people in the Pentagon's first units devoted to conducting cyber offense and defense operations. The deployment is part of a new mission which formalizes America's use of a class of weapons which the Obama administration has rarely discussed in public.
According to Carter, a physicist and former Harvard professor, future operations run by U.S. Cyber Command would be focused on these teams. "The teams are new, and they are in addition to the NSA work force. Twenty-seven of the 40 new teams will focus on cyber defenses," Alexander has said. Thirteen will be directed toward the creation of new cyber weapons. Edward Snowden made public a document which detailed a presidential directive signed by President Barack Obama providing guidelines for conducting both defensive and offensive operations. The president makes the decision whether or not to conduct cyber attacks.
That is only the tip of the iceberg. According to Greenwald, he and journalist Laura Poitras had obtained full sets of the documents during a trip to Hong Kong, where they met with Edward Snowden. The two journalists received some 10,000 top secret documents in total. Greenwald said that some of the documents were extremely complicated and are still being analyzed. He told Germany's Der Spiegel newspaper that some of the documents would be even "more explosive in Germany" than previous revelations. It will be interesting to see what the world makes of the new revelations, which are expected over the next few days.
The author is a columnist with China.org.cn. For more information please visit:
http://www.china.org.cn/opinion/zhaojinglun.htm
Opinion articles reflect the views of their authors, not necessarily those of China.org.cn.




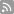
Go to Forum >>0 Comment(s)